RECENT BLOG NEWS
wolfSSL 5.8.0 Released
We are excited to announce that wolfSSL version 5.8.0 is now available. This release brings several important new features and improvements. Below are the key new additions:
New Features
- Implemented various fixes to support building for Open Watcom, including OS/2 support and Open Watcom 1.9 compatibility (PR 8505, 8484).
- Added support for STM32H7S (tested on NUCLEO-H7S3L8) (PR 8488).
- Added support for STM32WBA (PR 8550).
- Added Extended Master Secret Generation Callback to the –enable-pkcallbacks build (PR 8303).
- Implemented AES-CTS (–enable-aescts) in wolfCrypt (PR 8594).
- Added support for libimobiledevice commit 860ffb (PR 8373).
- Initial ASCON hash256 and AEAD128 support based on NIST SP 800-232 IPD (PR 8307).
- Added blinding option when using a Curve25519 private key by defining the macro WOLFSSL_CURVE25519_BLINDING (PR 8392).
ML-DSA and Post-Quantum Cryptography Enhancements
In line with NIST’s latest documentation, wolfSSL has updated its Dilithium implementation to ML-DSA (Module-Lattice Digital Signature Algorithm), which is fully supported in this release. Additionally, the release includes updates to further optimize ML-DSA and LMS (Leighton–Micali Signature) schemes, reducing memory usage and improving performance.
Linux Kernel Module (linuxkm) Updates
wolfSSL 5.8.0 expands support for the Linux Kernel Module (linuxkm), with several important enhancements to improve kernel-level cryptographic integration. This includes extended LKCAPI registration support for rfc4106(gcm(aes)), ctr(aes), ofb(aes), ecb(aes), and the legacy one-shot AES-GCM backend. Compatibility improvements have been added for newer kernels (?6.8), and calls to scatterwalk_map() and scatterwalk_unmap() have been updated for Linux 6.15. The release also registers ECDSA, ECDH, and RSA algorithms with the kernel crypto API and introduces safeguards for key handling, including forced zeroing of shared secrets. These changes make it possible to use more wolfSSL functionality in the kernel space.
For a full list of fixes and optimizations check out the ChangeLog.md bundled with wolfSSL. Download the latest release from the download page. If you have questions about any of the above, please contact us at facts@wolfSSL.com or call us at +1 425 245 8247.
Download wolfSSL Now
FIPS-Certified WireGuard
As WireGuard continues to grow in popularity for its simplicity and efficiency in VPN deployments, security-conscious organizations are increasingly demanding solutions that adhere to stringent security standards, such as FIPS 140-3 or CMMC 2.0. FIPS certification is a key requirement for governmental agencies and industries like defense and healthcare, where secure cryptographic implementations are mandatory and or in spaces where CMMC 2.0 compliance is a must. However, WireGuard’s default cryptographic implementations, while highly secure, are not FIPS-certified.
This is where wolfCrypt steps in. wolfCrypt is a lightweight, portable, and highly optimized cryptographic library that offers FIPS 140-3 certification, making it an ideal partner for users seeking FIPS compliance in their WireGuard deployments.
wolfCrypt FIPS integrates seamlessly with both the C and Go implementations of WireGuard, offering developers flexibility in choosing their preferred solution. For those using the C version of WireGuard, wolfCrypt can also be directly employed in kernel space via the wolfSSL kernel module.
So by leveraging our integration, users can gain access to a VPN solution that is both secure and FIPS-compliant. The performance of WireGuard, combined with the certified cryptographic operations of wolfCrypt, ensures that you don’t sacrifice speed or security. In fact, with wolfCrypt’s ability to utilize hardware acceleration, you might end up with a much faster WireGuard. Additionally, wolfCrypt’s small footprint makes it a practical choice for deployments in constrained environments, including IoT devices, embedded systems, and edge computing setups. You get a robust, certified security layer without bogging down performance.
Are you interested in WireGuard with wolfCrypt FIPS?
If you have questions about any of the above or need assistance, please contact us at facts@wolfSSL.com or call us at +1 425 245 8247.
Download wolfSSL Now
Broken Cryptographic Algorithms
wolfSSL’s wolfcrypt library includes several cryptographic algorithms that are now considered broken or deprecated. While these algorithms are typically disabled by default, developers should be aware of their security implications. Here is the list of these algorithms along with links to documents explaining why they are no longer considered secure:
- RC4/ARC4: Prohibited for TLS use due to keystream biases and practical attacks
- MD2: Moved to Historic Status due to collision attacks
- MD4: Moved to Historic Status, full collision attacks demonstrated
- MD5: Practical collision attacks, can generate collisions in seconds (See https://github.com/wolfSSL/wolfssl/pull/8895)
- SHA-1: Collision attacks demonstrated, officially retired by NIST in 2022
- DES: 56-bit key easily crackable by brute force attacks with modern hardware
- 3DES/TDEA: Deprecated by NIST, vulnerable to Sweet32 birthday attacks
- DSA: Being phased out by NIST, vulnerable to nonce reuse attacks
- RSA-1024 and weaker: There are experiments showing this is already too weak.
Note that these are still in the wolfSSL code base for some specific customer needs.
- Legacy Compatibility: Existing systems and embedded devices require these algorithms for interoperability
- Standards Compliance: Industry standards and regulatory requirements mandate support during transition periods
- Backward Compatibility: Applications migrating from legacy systems need continued support
- Gradual Migration Support: Organizations require time and pathways to transition to secure alternatives
NOTE: These algorithms are disabled by default and require explicit compilation flags (such as WOLFSSL_ALLOW_RC4) to enable them, demonstrating wolfSSL’s commitment to security best practices while maintaining necessary compatibility. There are other ways to enable some of these algorithms that you should be careful about:
- –enable-all will enable all these algorithms
- –enable-all-crypto will enable all these algorithms
- –enable-openssh will enable DSA
- –enable-wpas will enable DSA
- –enable-curl will enable DES3
- –enable-stunnel will enable DES3
- –enable-oldtls will enable MD5 and SHA-1
A great way to check if these algorithms are enabled is to inspect your wolfssl/options.h to see what macros are defined.
All that said, no matter how strong your algorithms are, if you have weak entropy or use weak parameters, your cryptography is eventually destined to fail. Another threat is quantum computers. As the state of the art improves in the field of quantum computing, so increases the risk to our currently considered secure algorithms. If you find these points confusing, please do reach out to us for guidance.
Please think very carefully before enabling any of these algorithms and please do reach out to us if you have any uncertainty with regards to whether you need them.
Here are some other algorithms that are considered broken:
- Dual_EC_DRBG: back-doored
- SIKE (Supersingular Isogeny Key Exchange): broken during NIST PQC competition
- Merkle–Hellman knapsack cryptosystem: broken by Shamir
- Caesar Cipher: vulnerable to brute force attacks and statistical analysis
If you have questions about any of the above, please contact us at facts@wolfSSL.com or call us at +1 425 245 8247.
Download wolfSSL Now
Enhancements to wolfCLU: PKCS8, Base64, and Improved Certificate Verification
We’re excited to announce recent improvements to wolfCLU, wolfSSL’s command line tool designed to make working with cryptographic data even easier and more flexible.
PKCS8 and Base64 Support
- pkcs8: Easily parse and handle PKCS#8-formatted private keys, ensuring compatibility with modern secure key formatting standards.
- base64: Encode or decode data in Base64 format directly from the command line.
Expanded Certificate Verification with -untrusted
The verif command now supports the -untrusted option, enabling verification of certificate chains that include intermediate CAs not directly trusted by the root. This makes wolfCLU a better fit for real-world PKI use cases where trust anchors and intermediates are handled separately.
Example:
$ ./wolfssl verify -in cert.pem -CAfile root.pem -untrusted intermediate.pem
Would you like to see more feature additions to wolfCLU?
If you have questions about any of the above, please contact us at facts@wolfssl.com or call us at +1 425 245 8247.
Download wolfSSL Now
Migrating to wolfSSL from mbedTLS
We wanted to highlight a useful migration guide posted by Amazon for their AWS IoT Core with FreeRTOS showing how to migrate from mbedTLS to wolfSSL. The migration guide shows useful API mappings and how to expose PKCS11 capabilities.
Check out the FreeRTOS with mbedTLS to FreeRTOS with wolfSSL Migration Guide v1.0.
FreeRTOS is a real-time operating system used in many embedded systems. It is lightweight and optimized for microcontrollers and small processors. For systems using cryptography or TLS, wolfSSL is a perfect match, so we wanted to highlight a guide for migrating from mbedTLS to wolfSSL.
The AWS IoT Core is a managed cloud service for secure, reliable communication between embedded devices and the AWS Cloud. The AWS Iot Core requires TLS communication to establish connections.
Why Migrate from mbedTLS to wolfSSL?
Moving to wolfSSL offers several advantages for embedded environments, including:
- Smaller footprint and performance optimizations: wolfSSL provides a reduced memory footprint and faster cryptographic processing.
- Latest Protocols: It also includes full support for TLS 1.3 and DTLS 1.3, enabling shorter handshakes and stronger encryption.
- Professional support: Direct support from engineers who authored and maintained the code. Free pre-sales support and paid support plans available.
- Commercial licensing: While open source, wolfSSL also offers commercial licenses for proprietary projects
- FIPS 140-3 certified cryptographic software module, making it suitable for regulated industries.
- Easy integration and extensive resources: The library includes detailed documentation and examples, simplifying testing and adoption.
- Expanded algorithm support: wolfSSL includes cryptographic algorithms beyond mbedTLS’s offerings such as Post Quantum (PQ) ML-DSA, ML-KEM, XMSS and LMSS.
- Assembly optimizations for ARM Cortex-M and A. We typically see a 10x speedup using our hand crafted assembly speedups, which are available for all our commonly used symmetric and asymmetric algorithms.
Note: This migration guide is fairly dated. Since then wolfSSL has developed and maintains full PKCS11 support to either consume a PKCS11 provider or to be one through our wolfPKCS11 provider. We also support using a TPM 2.0 module as the cryptographic and storage provider for wolfPKCS11.
If you have questions about any of the above, please contact us at facts@wolfSSL.com or call us at +1 425 245 8247.
Download wolfSSL Now
Live Webinar: The Basics of wolfBoot and All the Advanced Features We Have Recently Added
Secure your boot process with built-in post-quantum algorithms, hybrid crypto, and hardware-backed protection using wolfBoot.
Join us for the webinar, “The Basics of wolfBoot and the Advanced Features We Have Recently Added,” on July 9th at 9 AM PT. Presented by wolfSSL Senior Software Engineer Daniele Lacamera, this session introduces wolfBoot’s secure boot fundamentals and showcases new capabilities for cryptographic agility, platform expansion, and hardware trust integration.
Register Now: The Basics of wolfBoot and All the Advanced Features We Have Recently Added
Date: July 9th | 9 AM PT
wolfBoot is a lightweight, portable secure bootloader designed for embedded systems. It enables secure firmware updates, trusted execution, and cryptographic flexibility with wolfCrypt. In this webinar, you’ll learn how wolfBoot now supports post-quantum algorithms, hybrid secure boot schemes, HSM integration, and new hardware platforms that support next-generation cybersecurity requirements.
In this webinar, you’ll learn how to:
- Apply post-quantum algorithms (XMSS, LMS, ML-DSA) natively with wolfCrypt
- Combine classic and post-quantum algorithms in a hybrid secure boot implementation
- Leverage wolfHSM for secure key storage and cryptographic operations
- Deploy wolfBoot on Intel TigerLake to support x86-based platforms
- Harden Arm TrustZone-M environments with isolated cryptographic execution
Register now to strengthen your secure boot design with the latest advancements in wolfBoot.
As always, our webinar will include Q&A throughout. If you have questions about any of the above, please contact us at facts@wolfssl.com or call us at +1 425 245 8247.
Download wolfSSL Now
Cryptoagility
Have you heard the newest and most pervasive buzzword in online security? Recently, the most popular and over-hyped expression doing the rounds these days is “Cryptoagility”. Why do we think it is so overhyped? Because if you are simply looking for a definition, you’ll be hard pressed to find one. People who talk about it can barely define it.
Most will have you believe in a vague notion of being able to swap out algorithms in real time via the click of a mouse button. No need for reboots, updates or interference from system administrators. Some will even go as far as having the ability to swap different implementations of the same algorithms. Uber flexibility in the runtime environment.
Here at wolfSSL we have a more nuanced approach to cryptoagility. What we just described above is what we call RuntimebCryptoagility and if your system can accommodate it and you are willing to spend the resources to have it, then perhaps you might want to look into our wolfEngine and wolfProvider products.
The other kind of Cryptoagility where the wolfSSL team specializes in is Buildtime Cryptoagility. We recognize that when it comes to embedded systems, resources are at a premium and can not be wasted. With that in mind, currently unused algorithms and data are taking up valuable memory and footprint. For example, if you’re planning a post-quantum transition, having those algorithms in your firmware now might not be practical. With wolfBoot, our super efficient boot loader implementation, that migration is a simple and seamless firmware update away. When the time comes, rebuild your firmware with the algorithms required and have a seamless Cryptoagility experience.
Note that it has been this way for years. Here at wolfSSL, we didn’t need to create a new buzzword to serve our customers.
If you have questions about any of the above, please contact us at facts@wolfssl.com or call us at +1 425 245 8247.
Download wolfSSL Now
Coming Soon: tiny-curl for Zephyr RTOS
At wolfSSL, we’re excited to announce plans for a tiny-curl port tailored for Zephyr RTOS. This will bring lightweight HTTPS client capabilities to one of the most widely used real-time operating systems for embedded devices.
Stay tuned for updates as we work to integrate tiny-curl’s proven functionality into the Zephyr ecosystem.
If you have questions about any of the above, please contact us at facts@wolfSSL.com or call us at +1 425 245 8247.
Download wolfSSL Now
Retrofitting Legacy Bootloaders with wolfBoot: a Modern Secure Bootloader for Embedded Systems
Introduction: Modernizing Legacy Devices with Secure Boot
Embedded developers often face the challenge of adding a secure bootloader for embedded systems to legacy hardware without overhauling the entire boot process. Many automotive and industrial devices – for example, older PowerPC-based electronic control units (ECUs) in vehicles or aging industrial controllers – still run insecure or outdated bootloaders. These legacy bootloaders may lack any firmware authentication, leaving devices vulnerable to malicious firmware replacement. Replacing them entirely can be risky and costly, especially if the existing boot code contains years’ worth of custom logic (like proprietary network protocols or special hardware init routines). Fortunately, wolfBoot provides a solution to retrofit secure boot in legacy devices without starting from scratch. In fact, many companies upgrading older products have successfully added a secure boot solution using wolfBoot while reusing their legacy software. wolfBoot’s flexibility allows it to be integrated as a static library alongside your current bootloader code, enhancing security through firmware signing and verification without requiring a full redesign. This post will explore how wolfBoot can seamlessly augment legacy boot processes – for automotive ECUs, industrial systems, and more – by acting as a drop-in secure boot component. We’ll also highlight wolfBoot’s unique features (ELF parsing, delta updates, post-quantum cryptography, TPM integration, etc.) that set it apart from typical alternatives.
Integrating wolfBoot as a Static Library in Existing Bootloaders
One of wolfBoot’s key strengths is its ability to integrate into existing bootloaders as a static library. Rather than mandating a wholesale replacement of your boot code, wolfBoot can be compiled into a single object and called from your current bootloader flow. This means you can enhance firmware signing and verification in your device’s boot process by simply invoking wolfBoot’s API, without rewriting your platform initialization, device drivers, or update logic.
wolfBoot’s library mode provides straightforward interfaces to do things like parse the firmware’s cryptographic manifest header, check version numbers for anti-rollback, and verify the integrity and authenticity of a firmware image that’s already been loaded or mapped in memory. Essentially, wolfBoot handles the security-critical steps (signature verification, hash checking, version enforcement) while your legacy bootloader can continue to do what it already does well (hardware setup, communication, firmware loading). The wolfBoot host tools for key management and firmware signing (such as the keygen and sign utilities) remain the same as those used in stand-alone wolfBoot deployments. This means you don’t have to reinvent your signing process – you can reuse the proven wolfBoot tooling to generate keys and sign firmware images offline, and then have your integrated wolfBoot code verify those images on the device. The firmware image format (with its signed manifest) stays consistent, independent of your hardware or architecture, which simplifies integration and testing.
By integrating wolfBoot’s static library, product engineers can replace a legacy bootloader in automotive ECUs or other systems incrementally. For example, if you have an existing boot flow in a car’s ECU that loads an application from flash, you can incorporate wolfBoot’s verification function right before jumping to the application. wolfBoot will check the cryptographic signature of the firmware using a public key (stored securely on the device), and only boot it if it’s authentic and not revoked. This approach drastically improves security with minimal changes to your codebase – you preserve all your custom boot logic and simply add a call to wolfBoot for the security check. As the wolfSSL team notes, starting a new bootloader from scratch is often underestimated in effort, so this augment-not-replace strategy is a huge win for development time. In short, wolfBoot’s library mode allows retrofitting a secure bootloader in legacy devices elegantly, bringing modern cryptographic boot verification to platforms that were never originally designed for it.
Use Case: Legacy Automotive and Industrial Systems
Legacy automotive and industrial systems highlight the value of wolfBoot’s flexible integration. Consider an automotive ECU built on an older PowerPC or ARM9 processor – it might be running a manufacturer-specific bootloader from decades ago. Such an ECU could be responsible for critical functions (engine control, braking, etc.) and thus a prime target for firmware tampering if left unsecured. Using wolfBoot, the development team can retrofit secure boot into this ECU without rewriting the time-tested OEM boot code. wolfBoot, compiled as a static library, can be invoked to authenticate the firmware update whenever the vehicle powers on or receives new firmware over-the-air. The ECU gains modern firmware signing and verification (e.g., ECC or RSA signatures with SHA-256 hashes) overnight, hardening it against unauthorized code. All the while, existing functionalities – whether a CAN bus bootloader protocol or a custom fail-safe routine – remain intact around the wolfBoot calls.
Similarly, in industrial IoT devices or PLCs that often have long lifecycles, wolfBoot can be integrated to replace legacy bootloaders that have no security. For instance, an industrial controller that loads its program from external flash can have wolfBoot inserted to verify that program’s signature before execution. This ensures that even if someone manages to drop in a malicious firmware, the device will reject it and prevent potentially catastrophic equipment behavior. In both automotive and industrial contexts, wolfBoot’s small footprint and quick verification (a signature check takes only a fraction of a second on typical microcontrollers) means added security doesn’t significantly delay boot time or require hardware upgrades. It’s a cost-effective path to meeting modern security standards (such as ISO 26262 in automotive or IEC 62443 in industrial control) by building on top of legacy infrastructure.
Unique Features of wolfBoot for Secure Boot Retrofits
While ease of integration is a major advantage, wolfBoot also brings a rich set of unique features that are not commonly found together in other bootloaders. These features not only solve typical secure boot needs (authenticating firmware), but also provide advanced capabilities that can future-proof your device’s update system and security architecture. Below are some of the standout features of wolfBoot and why they matter when upgrading legacy systems:
- Delta Updates (Incremental OTA): wolfBoot supports incremental firmware updates, meaning you can apply “delta” updates that contain only the binary differences between the new firmware and the current one.
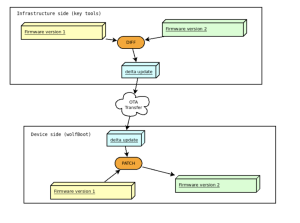
This is extremely useful for legacy devices operating on low-bandwidth networks or with limited flash storage. Instead of transferring a full firmware image for every update, a tiny patch can be sent and applied on-device. The wolfBoot signing tool can generate a cryptographically signed patch file that the bootloader uses to reconstruct the new firmware from the old version. WolfBoot verifies the update package’s authenticity before applying the patch and then verifies the final patched firmware after applying it, ensuring end-to-end integrity. This two-step verification and the reduced update size result in faster, reliable over-the-air (OTA) updates – a major plus for legacy devices on constrained links. (For instance, industrial sensors on LPWAN networks or remote automotive ECUs can be updated without pulling them out of service for long periods.) - ELF Parsing and Scattered Section Support: Unlike many bootloaders that expect a flat binary, wolfBoot can directly load and authenticate ELF-format images, including those with scattered memory sections. This is particularly helpful when retrofitting systems that produce ELF firmware outputs (such as RTOS or Linux kernel images). wolfBoot’s loader understands complex image layouts – it supports booting raw binaries, Linux kernels, and even Multiboot2/ELF formatted images. As a result, you can secure a wider range of firmware types without extra post-processing. Legacy devices that have unusual memory maps or segmented firmware can still use wolfBoot for verification without repackaging everything into a single blob.
- Hybrid Post-Quantum Cryptography (PQC) + Classic Signatures: Security longevity is a concern for any device being retrofitted now, as these devices might remain in the field for many years. wolfBoot stays ahead of the curve by supporting post-quantum signature schemes (stateful hash-based signatures like LMS/HSS and XMSS) alongside traditional algorithms. In fact, wolfBoot allows hybrid authentication, where a firmware image can be signed with both a classic algorithm (say ECDSA or RSA) and a PQC algorithm simultaneously. The bootloader will accept the image if either signature verifies. This dual-signature approach means you can deploy firmware updates that are secure against both today’s threats and future quantum attacks. It’s a rare feature that positions legacy hardware for the post-quantum era – ensuring that retrofitted ECUs or controllers aren’t the weak link a decade from now when quantum computers emerge.
- TPM 2.0 Integration via wolfTPM (Measured Boot): wolfBoot can leverage Trusted Platform Module hardware (TPM 2.0) to enhance secure boot through measured boot and secure key storage. Through integration with the wolfTPM library, wolfBoot can utilize a TPM as a root of trust at boot time. For example, wolfBoot can extend TPM Platform Configuration Registers (PCRs) with measurements of the boot process, enabling remote attestation of exactly what firmware was booted. It can also use the TPM to seal secrets (like encryption keys) that only unseal if the correct firmware is running. This means that on devices equipped with a TPM – common in automotive gateways or high-end industrial controllers – wolfBoot can provide an even higher level of security, guaranteeing that even the bootloader itself hasn’t been tampered with. Additionally, wolfBoot’s TPM support allows storing the public keys or hash of the expected firmware in tamper-resistant hardware, preventing an attacker with physical access from altering the trust anchors. These capabilities go beyond simple signature checking, moving into the realm of hardware-based device trust, which is seldom found in off-the-shelf bootloaders. (wolfBoot inherits these capabilities from wolfCrypt and wolfTPM, so developers get the benefits without having to write any low-level TPM code themselves.)
- Broad Platform Support and Portability: wolfBoot is designed to be highly portable and has been successfully run on an extremely wide range of hardware – from tiny Arm Cortex-M0+ microcontrollers all the way up to 64-bit x86 processors like the latest Intel platforms (e.g., Intel Raptor Lake). It has virtually no external dependencies (it doesn’t require an OS or complex runtime, just the wolfCrypt crypto library). This means whether your legacy device is a small bare-metal sensor node or a more powerful embedded Linux system, wolfBoot can likely be adapted to it. Out of the box, wolfBoot supports architectures including ARM (Cortex-M and A profiles), MIPS, RISC-V, x86, and PowerPC – covering most legacy CPU types found in automotive and industrial devices. In fact, wolfBoot’s existing hardware abstraction layer (HAL) only consists of a handful of functions (for flash read/write, booting the image, etc.), making new ports straightforward. Its minimal footprint (on the order of a few kilobytes of flash and memory) ensures it can fit in systems with tight resource constraints. This broad compatibility and light weight are critical for retrofitting; you can introduce wolfBoot into legacy designs without worrying about hardware incompatibilities or resource exhaustion. Many open-source bootloaders or OEM solutions struggle to support such diverse environments or carry OS-specific baggage – by contrast, wolfBoot’s agnostic design lets it drop in virtually anywhere.
- Minimal External Dependencies: As noted, wolfBoot does not depend on any heavyweight frameworks or operating systems. It uses wolfSSL’s proven wolfCrypt library for cryptographic functions and otherwise runs standalone. There’s no need for libc or dynamic memory allocation (unless you choose to enable such features). For an engineer retrofitting an old system, this is a relief – you don’t have to pull in a large RTOS or file system code just to get secure boot. This also means fewer potential points of failure. wolfBoot’s slim design makes it easier to validate and certify as part of a system (which leads into its readiness for formal certification, below). The lack of external dependencies also simplifies maintenance: you only update the cryptography library (to get the latest security algorithms or patches) and wolfBoot itself when needed, without entangling other software components.
- FIPS 140-Ready and DO-178C Certifiability: wolfBoot is built with high-assurance industries in mind. It can be compiled to use a FIPS 140-3 validated cryptographic module (wolfCrypt) for signature verification, which is crucial for government and defense applications that require FIPS-certified security. The design and development processes of wolfBoot also align with safety-critical standards. Notably, wolfSSL (the developer of wolfBoot) offers support for RTCA DO-178C DAL A certification – meaning the core cryptography and bootloader can come with the artifacts needed for avionics or other safety-critical certifications. This is a significant advantage if you plan to use wolfBoot in aerospace, automotive (ISO 26262), or industrial (IEC 61508) projects where certification is mandatory. Most open-source bootloaders were never intended for this level of compliance. In contrast, wolfBoot’s pedigree (developed by a security-focused company with certification experience) means it’s ready to be taken through rigorous certification processes. By retrofitting a legacy device with wolfBoot, you not only get a security upgrade, but you also get a path towards meeting regulatory requirements for cryptographic modules and software development standards – a key strategic consideration for product longevity and market compliance.
A Flexible, Future-Proof Secure Boot Solution
In summary, wolfBoot provides a flexible and mature secure bootloader solution for embedded systems, ideal for breathing new life into legacy bootloader environments. Its integration-as-a-library approach lets you add firmware signing and verification to existing boot processes with minimal changes, avoiding the cost and risk of a full rewrite. WolfBoot’s rich feature set – from ELF image support and reliable update/rollback mechanisms to cutting-edge crypto like post-quantum signatures and TPM-based measured boot – means you’re not just patching a hole in your legacy system, you’re uplifting it to state-of-the-art security. Importantly, wolfBoot achieves all this while remaining lightweight, hardware-agnostic, and easy to port, so it compares favorably to traditional bootloaders that might require extensive customization or lack such advanced capabilities.
By choosing wolfBoot to replace a legacy bootloader in automotive ECUs or other devices, product engineers gain a production-hardened boot security layer backed by wolfSSL’s extensive experience in embedded security (wolfSSL’s crypto is already in billions of devices). This gives confidence in the solution’s reliability and support. In practical terms, deploying wolfBoot in a legacy device means that every boot and firmware update is guarded by modern cryptography and best practices. The device will only run trusted code, mitigating the risk of bricking or malicious control – a non-negotiable requirement in today’s security-conscious landscape.
For developers, wolfBoot strikes an excellent balance between technical depth and integration simplicity. Strategically, it extends the lifespan and safety of legacy product lines, letting you retrofit secure boot in legacy devices to meet current security demands and even anticipate future ones. If you’re looking to modernize an existing embedded system’s boot process without a ground-up redesign, wolfBoot offers a proven path to achieve firmware signing and verification, robust updates, and a foundation of trust from power-on to application launch. Embracing wolfBoot is an investment in your device’s security future – ensuring that even your oldest devices can boot with the confidence of a modern, secure bootloader for embedded systems.
Learn more: You can find additional information and documentation on wolfBoot’s features and integration process on the official wolfSSL website and GitHub. With wolfBoot, retrofitting security into legacy bootloaders is no longer an uphill battle, but a straightforward enhancement to ensure your embedded devices start safe and stay secure.
If you have questions about any of the above, please contacts us at facts@wolfssl.com or call us at +1 425 245 8247.
Download wolfSSL Now
Securing UEFI with wolfSSL’s FIPS 140-3 Cryptography
One of the biggest strengths of the wolfSSL portfolio is its ability to adapt and run in the most diverse environments, whether it’s a minimal bare-metal deployment or a complex, multi-layered operating system.
This blog highlights recent improvements in the wolfSSL products regarding integration with the Unified Extensible Firmware Interface (UEFI)—the modern way to interface with hardware firmware during the initial steps after booting a machine (UEFI has replaced the legacy BIOS).
wolfSSL can already enhance UEFI firmware with component authentication and secure updates, as wolfBoot—our secure boot solution—can run as a UEFI application inside UEFI environments (Check out the build instruction).
Recently, wolfSSL has made it even simpler for other UEFI applications to access wolfSSL cryptographic services (using wolfCrypt). wolfSSL has improved its use of UEFI features, leveraging TRNG and crypto accelerators exposed by UEFI.
UEFI applications can now consume a FIPS 140-3 certified range of wolfSSL cryptographic algorithms (AES, RSA, DSA, ECDSA, SHA), key derivation functions, and secure communication protocols (D)TLS up to v1.3.
As a leader in embedded FIPS certificates, wolfSSL can assist you in the certifying of your UEFI based operating environments (OE’s) and assists you in the ACVP (Automated Cryptographic Validation Protocol).
The use cases are many: OS-agnostic secure communication, TPM attestation, disk encryption, and more.
If you are interested in using wolfSSL cryptography, wolfSSL TLS communication, any wolfSSL product inside a UEFI environment, or have questions about any of the above, please contact us at facts@wolfSSL.com or call us at +1 425 245 8247.
Download wolfSSL Now
wolfHSM Support for Renesas RH850
We’re happy to announce that we’ve added support for Renesas RH850 in wolfHSM.
The RH850 Family of 32-bit automotive microcontrollers (MCUs) is an automotive microcontroller equipped with an integrated Hardware Security Module (HSM). It ensures fast and secure key management, cryptographic processing, and authentication at the hardware level. Designed for next-generation ECUs, it combines functional safety with advanced security.
wolfHSM is a framework that combines the cryptographic algorithms provided by the processor with software cryptographic processing by wolfCrypt, allowing you to flexibly extend the crypt algorithms as needed.
wolfSSL has now ported wolfHSM on Renesas RH850 F1KM. RH850 F1KM supports true random number generation and the AES block cryptographic algorithm on the HSM core. The wolfHSM client running on the main core requests cryptographic processing to the wolfHSM server running on the HSM core through shared memory. Random number generation and AES cryptographic processing can be offloaded to the HSM core. In addition, it is possible to delegate key generation and storage for public key cryptography algorithms to the HSM core. The generated keys are securely protected in flash managed by the HSM core.
If you are interested in porting wolfHSM to the RH850, including a sample wolfHSM server and client, or if you have questions about any of the above, please contact us at facts@wolfssl.com or call us at +1 425 245 8247.
Download wolfSSL Now
Weekly updates
Archives
- July 2025 (8)
- June 2025 (22)
- May 2025 (25)
- April 2025 (24)
- March 2025 (22)
- February 2025 (21)
- January 2025 (23)
- December 2024 (22)
- November 2024 (29)
- October 2024 (18)
- September 2024 (21)
- August 2024 (24)
- July 2024 (27)
- June 2024 (22)
- May 2024 (28)
- April 2024 (29)
- March 2024 (21)
- February 2024 (18)
- January 2024 (21)
- December 2023 (20)
- November 2023 (20)
- October 2023 (23)
- September 2023 (17)
- August 2023 (25)
- July 2023 (39)
- June 2023 (13)
- May 2023 (11)
- April 2023 (6)
- March 2023 (23)
- February 2023 (7)
- January 2023 (7)
- December 2022 (15)
- November 2022 (11)
- October 2022 (8)
- September 2022 (7)
- August 2022 (12)
- July 2022 (7)
- June 2022 (14)
- May 2022 (10)
- April 2022 (11)
- March 2022 (12)
- February 2022 (22)
- January 2022 (12)
- December 2021 (13)
- November 2021 (27)
- October 2021 (11)
- September 2021 (14)
- August 2021 (10)
- July 2021 (16)
- June 2021 (13)
- May 2021 (9)
- April 2021 (13)
- March 2021 (24)
- February 2021 (22)
- January 2021 (18)
- December 2020 (19)
- November 2020 (11)
- October 2020 (3)
- September 2020 (20)
- August 2020 (11)
- July 2020 (7)
- June 2020 (14)
- May 2020 (13)
- April 2020 (14)
- March 2020 (4)
- February 2020 (21)
- January 2020 (18)
- December 2019 (7)
- November 2019 (16)
- October 2019 (14)
- September 2019 (18)
- August 2019 (16)
- July 2019 (8)
- June 2019 (9)
- May 2019 (28)
- April 2019 (27)
- March 2019 (15)
- February 2019 (10)
- January 2019 (16)
- December 2018 (24)
- November 2018 (9)
- October 2018 (15)
- September 2018 (15)
- August 2018 (5)
- July 2018 (15)
- June 2018 (29)
- May 2018 (12)
- April 2018 (6)
- March 2018 (18)
- February 2018 (6)
- January 2018 (11)
- December 2017 (5)
- November 2017 (12)
- October 2017 (5)
- September 2017 (7)
- August 2017 (6)
- July 2017 (11)
- June 2017 (7)
- May 2017 (9)
- April 2017 (5)
- March 2017 (6)
- January 2017 (8)
- December 2016 (2)
- November 2016 (1)
- October 2016 (15)
- September 2016 (6)
- August 2016 (5)
- July 2016 (4)
- June 2016 (9)
- May 2016 (4)
- April 2016 (4)
- March 2016 (4)
- February 2016 (9)
- January 2016 (6)
- December 2015 (4)
- November 2015 (6)
- October 2015 (5)
- September 2015 (5)
- August 2015 (8)
- July 2015 (7)
- June 2015 (9)
- May 2015 (1)
- April 2015 (4)
- March 2015 (12)
- January 2015 (4)
- December 2014 (6)
- November 2014 (3)
- October 2014 (1)
- September 2014 (11)
- August 2014 (5)
- July 2014 (9)
- June 2014 (10)
- May 2014 (5)
- April 2014 (9)
- February 2014 (3)
- January 2014 (5)
- December 2013 (7)
- November 2013 (4)
- October 2013 (7)
- September 2013 (3)
- August 2013 (9)
- July 2013 (7)
- June 2013 (4)
- May 2013 (7)
- April 2013 (4)
- March 2013 (2)
- February 2013 (3)
- January 2013 (8)
- December 2012 (12)
- November 2012 (5)
- October 2012 (7)
- September 2012 (3)
- August 2012 (6)
- July 2012 (4)
- June 2012 (3)
- May 2012 (4)
- April 2012 (6)
- March 2012 (2)
- February 2012 (5)
- January 2012 (7)
- December 2011 (5)
- November 2011 (7)
- October 2011 (5)
- September 2011 (6)
- August 2011 (5)
- July 2011 (2)
- June 2011 (7)
- May 2011 (11)
- April 2011 (4)
- March 2011 (12)
- February 2011 (7)
- January 2011 (11)
- December 2010 (17)
- November 2010 (12)
- October 2010 (11)
- September 2010 (9)
- August 2010 (20)
- July 2010 (12)
- June 2010 (7)
- May 2010 (1)
- January 2010 (2)
- November 2009 (2)
- October 2009 (1)
- September 2009 (1)
- May 2009 (1)
- February 2009 (1)
- January 2009 (1)
- December 2008 (1)

